Fully Compliant, Strikingly Simple
Designed from the ground-up to comply with the stringest requirements of the Life Sciences industry.
Efficiently guarantee the Confidentiality, Integrity, and Availability of your company's data by adopting a customizable Information Security Management System that can be made operational in less than a day!
Strengths

Intuitive and usable interface
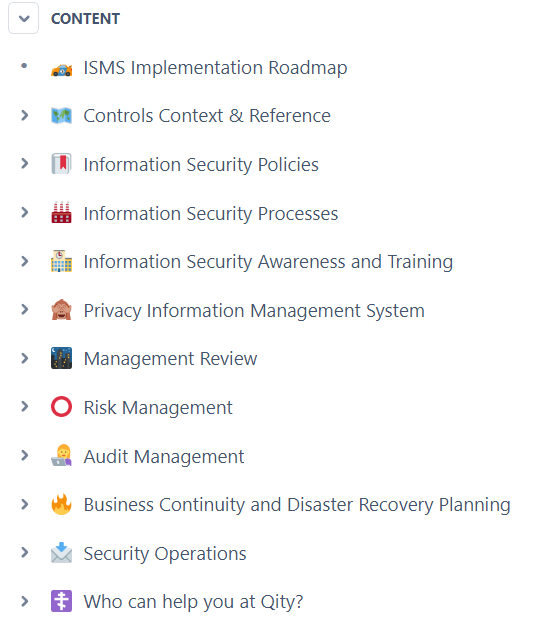
Experience seamless integration and management of your security protocols with our user-friendly Integrated Security Management System (ISMS). Designed with intuitiveness at its core, our ISMS offers a straightforward and efficient way to oversee your security measures.
Its intuitive interface ensures that you can effortlessly navigate through the system, making the complex world of compliance and risk management accessible to everyone in your organization. Embrace simplicity without sacrificing sophistication, and take control of your security with ease.

Out-of-the-box Compliance
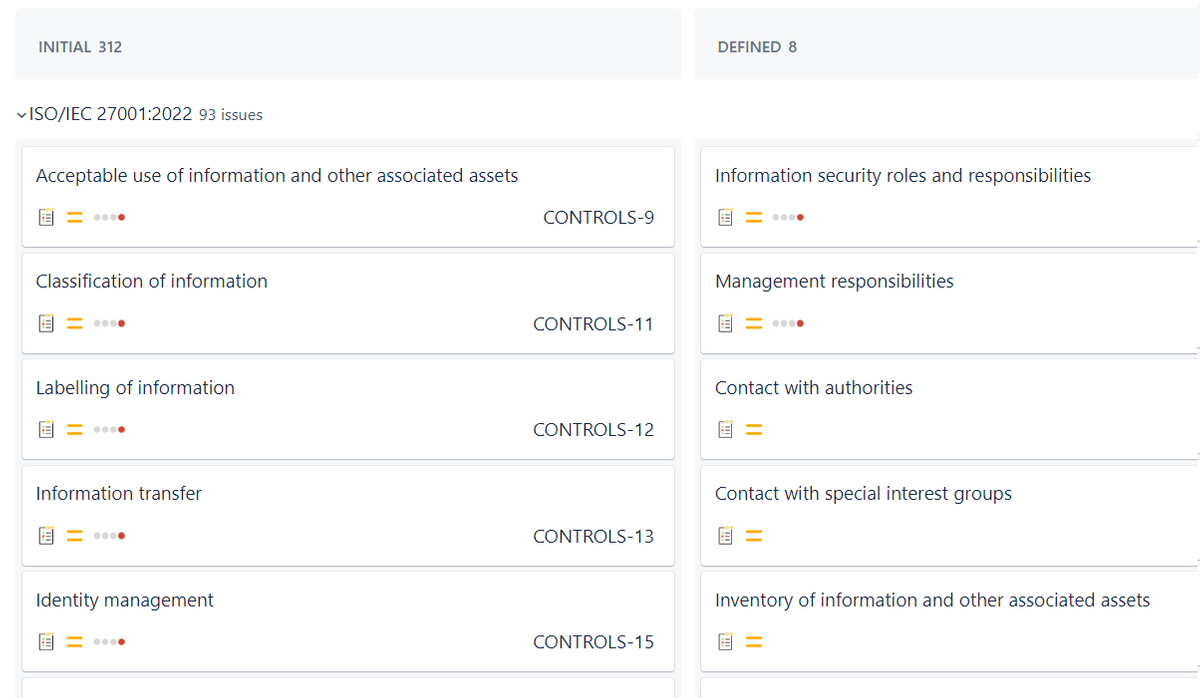
Streamline your workflow effortlessly with Qity's Standards and Regulations Control package which includes ISO/IEC 27001:2022, 27005:2022, 27701:2019, ISO 14971:2019, NIS 2 Directive and NIST SP 800-53.
With just a single click, instantly check the progress of control implementations and directly pinpoint evidence of implementation from within the control itself, saving you countless hours of manual work.

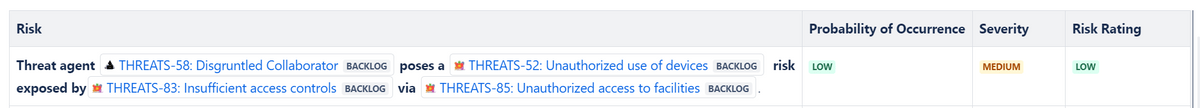
Visualize Full Risk vectors
Dynamically generate Risk Register information based on related Threat Agents, Attack Vectors, Vulnerabilities, and Non-Compliances to visualize which threats you should prioritize mitigating first.

Manage Audits and Correction Plans
Dynamically generate Risk Register information based on related Threat Agents, Attack Vectors, Vulnerabilities, and Non-Compliances to visualize which threats you should prioritize mitigating first.

Seemlessly integrate with your QMS
Dynamically generate Risk Register information based on related Threat Agents, Attack Vectors, Vulnerabilities, and Non-Compliances to visualize which threats you should prioritize mitigating first.
How It Works
Add subtitle
1Purchase
Pick your favorites from our high-quality collections, and add to your cart.2Pay Online
Enter your address and pay with credit, debit, or PayPal. We ship anywhere.3Deliver
We'll deliver your goods within 5 business days. Ask us any questions!- Contact UsDon't be afraid to reach out. You + us = awesome.